Duane Morris Takeaway: Class action lawsuits and mass arbitrations alleging cybersecurity incidents and data privacy violations are rising exponentially. Corporate counsel seeking to deter such litigation and arbitration demands from being filed against their companies should keep in mind the following four best practices: (1) add or update arbitration clauses to mitigate the risks of mass arbitration; (2) use cybersecurity best practices, including continuously improving and prioritizing compliance activities; (3) audit and adjust uses of website advertising technologies; and (4) update website terms of use, data privacy policies, and vendor agreements.
Best Practices
- Add or update arbitration agreements to mitigate the risks of mass arbitration
Many organizations have long been familiar with the strategy of deterring class and collective actions by presenting arbitration clauses containing class and collective action waivers prominently for web users, consumers, and employees to accept via click wrap, browse wrap, login wrap, shrink wrap, and signatures. Such agreements would require all allegedly injured parties to file individual arbitrations in lieu of any class or collective action. Moreover, the strategy goes, filing hundreds, thousands, or more individual arbitrations would be cost-prohibitive for so many putative plaintiffs and thus deter them from taking any action against the organization in most cases.
Over the last decade, this strategy of deterrence was effective.[1] Times have changed. Now enterprising plaintiffs’ attorneys with burgeoning war chests, litigation funders, and high-dollar novel claims for statutory damages are increasingly using mass arbitration to pressure organizations into agreeing to multimillion dollar settlements, just to avoid the arbitration costs. In mass arbitrations filed with the American Arbitration Association (AAA) or Judicial Arbitration and Mediation Services (JAMS), for example, fees can total millions of dollars just to defend only 500 individual arbitrations.[2] One study found upfront fees ranging into the tens of millions of dollars for some large mass arbitrations.[3] Companies with old arbitration clauses have been caught off guard with mass arbitrations, have sought relief from courts to avoid having to defend these mass arbitrations, and this relief was rejected in several recent decisions where the court ordered the defendant to arbitrate and pay the required hefty mass arbitration fees.[4]
If your organization has an arbitration clause, then one of the first challenges for counsel defending many newly served class action lawsuits these days is determining whether to move to compel arbitration. Although it could defeat the class action, is it worth the risk of mass arbitration and the potential projected costs of mass arbitration involved? Sometimes not.
Increasingly organizations are mitigating this risk by including mechanisms in their arbitration clauses such as pre-dispute resolution clauses, mass arbitration waivers, bellwether procedures, arbitration case filing requirements, and more. This area of the law is developing quickly. One case to watch will be one of the first appellate cases to address the latest trend of mass arbitrations — Wallrich v. Samsung Electronics America, Inc., No. 23-2842 (7th Cir.) (argued February 15, 2024, at issue is whether the district court erred in ordering the BIPA defendant to pay over $4 million in mass arbitration fees).
- Use cybersecurity best practices, including continuously improving and prioritizing
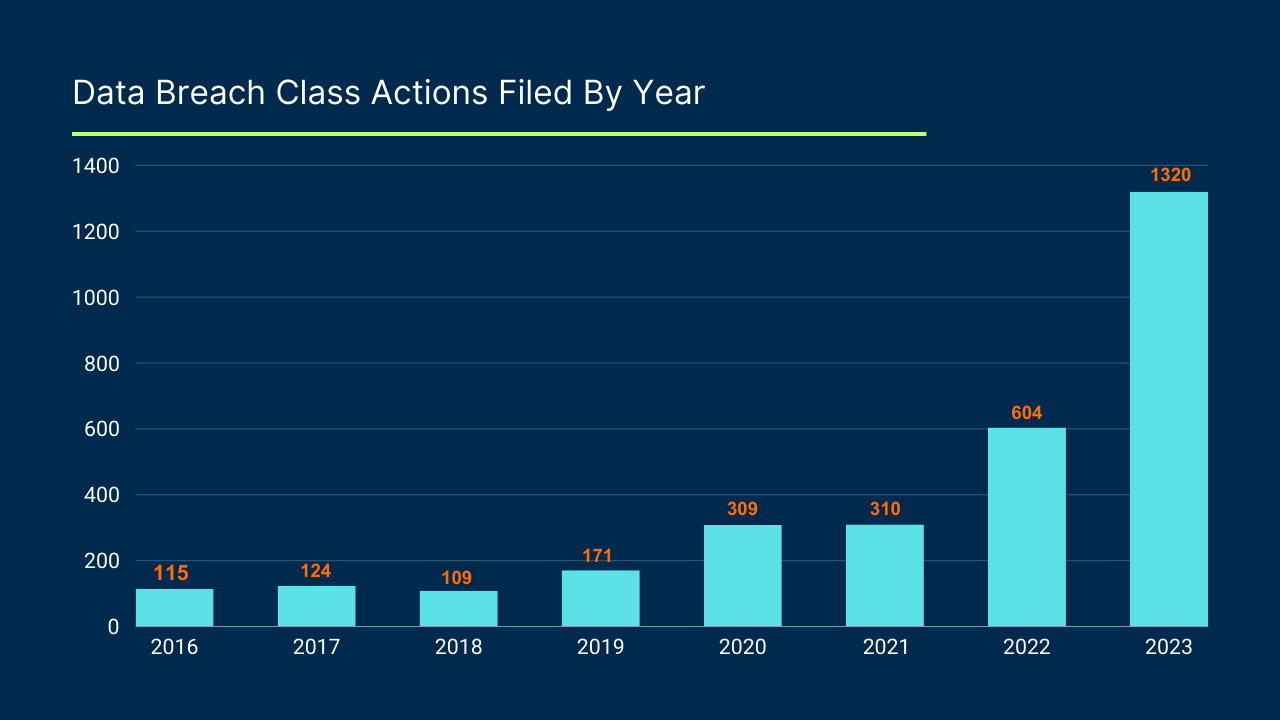
IT organizations have long been familiar with the maxim that they should continuously improve their cybersecurity measures and other IT services. Continuous improvement is part of many IT industry guidelines, such as ISO 27000, COBIT, ITIL, the NIST Cybersecurity Framework (CSF) and Special Publication 800, and the U.S. Department of Energy’s Cybersecurity Capability Maturity Model (C2M2). Continuous improvement is becoming increasingly necessary in cybersecurity, as organizations’ IT systems and cybercriminals’ tools multiply at an increased rate. The volume of data breach class actions doubled three times from 2019-2023:
Continuous improvement of cybersecurity measures needs to accelerate accordingly. As always, IT organizations need to prioritize. Priorities typically include:
- improving IT governance;
- complying with industry guidelines such as ISO, COBIT, ITIL, NIST, and C2M2;
- deploying multifactor authentication, network segmentation, and other multilayered security controls;
- staying current with identifying, prioritizing, and patching security holes as new ones continuously arise;
- designing and continuously improving a cybersecurity incident response plan;
- routinely practicing handling ransomware incidents with tabletop exercises (may be covered by cyber-insurers); and
- implementing and continuously improving security information and event management (SIEM) systems and processes.
Measures like these to continuously improve and prioritize: (a) will help prevent a cybersecurity incident from occurring in the first place; and (b) if one occurs, will help the victim organization of cybertheft defend against plaintiffs’ arguments that the organization failed to use reasonable cybersecurity measures.
- Audit and adjust uses of website advertising technologies
In 2023, plaintiffs filed over 250 class actions alleging that Meta Pixel, Google Analytics, and other similar software embedded in defendants’ websites secretly captured plaintiffs’ web browsing data and sent it to Meta, Google, and other online advertising agencies, respectively. This software, often called website advertising technologies or “adtech” (and often referred to by plaintiffs as “tracking technologies”) is a common feature on many websites in operation today — millions of companies and governmental organizations have it.[5] These lawsuits generally allege that the organization’s use of adtech violated federal and state wiretap statutes, consumer fraud statutes, and other laws, and often seek hundreds of millions of dollars in statutory damages. The businesses targeted in these cases so far mostly have been healthcare providers but also span nearly every industry including retailers, consumer products, and universities.
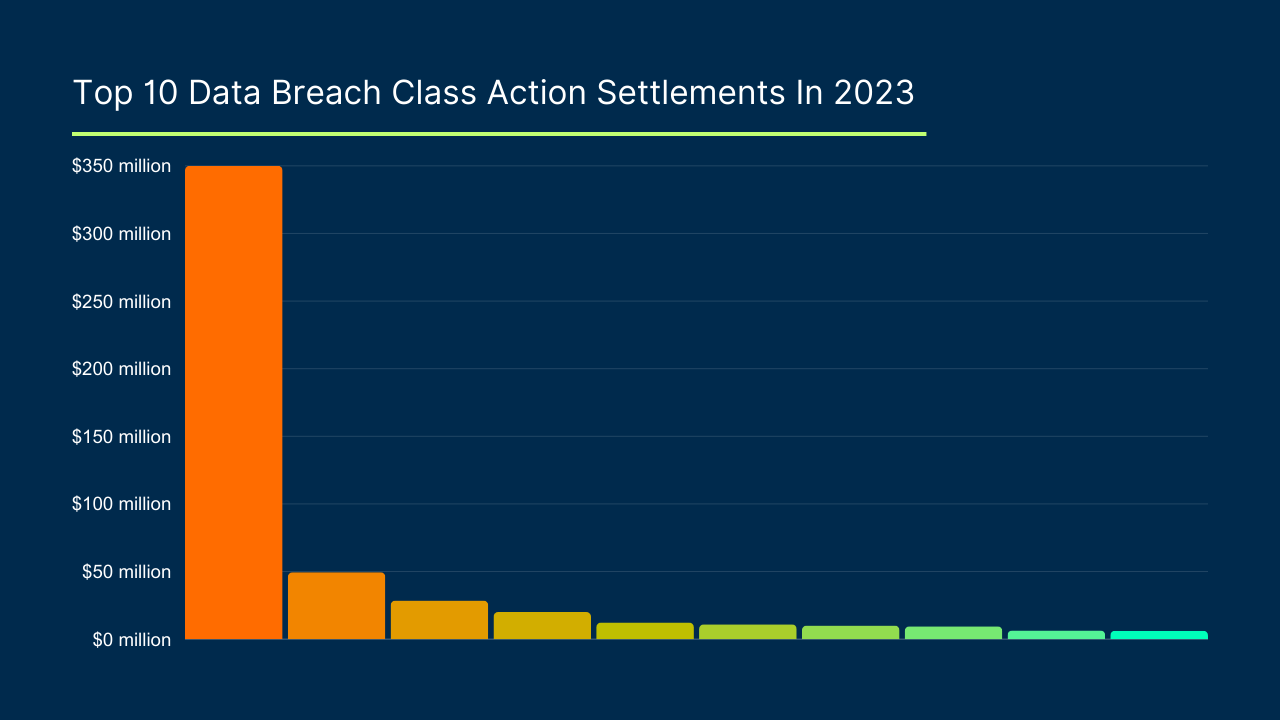
Several of these cases have resulted in multimillion-dollar settlements, several have been dismissed, and the vast majority remain undecided. The legal landscape in this area has only begun to develop under many plaintiffs’ theories of liability, statutes, and common laws. The adtech alleged has included not only Meta Pixel and Google Analytics but also dozens of the hundreds or thousands of other types of adtech. All this legal uncertainty multiplied by requested statutory damages equals serious business risk to any organization with adtech on its public-facing website(s).
An organization may not know that adtech is present on its public-facing websites. It could have been installed on a website by a vendor without proper authorization, for example, or as a default without any human intent by using some web publishing tools.
Organizations should consider whether to have an audit performed before any litigation arises as to which adtech is or has been installed on which web pages when and which data types were transmitted as a result. Multiple experts specialize in such adtech audits and serve as expert witnesses should any litigation arise. An adtech audit is relatively quick and inexpensive and it might be cost-beneficial for an organization to perform an adtech audit before litigation arises because: (a) it might convince an organization to turn off some of its unneeded adtech now, thereby cutting off any potential damages relating to that adtech in a future lawsuit; (b) in the event of a future lawsuit, such an audit would not be wasted — it is one of the first things adtech defendants typically perform upon being served with an adtech lawsuit; and (c) an adtech audit could assist in presently updating and modernizing website terms of use, data privacy policies, and vendor agreements (next topic).
- Update and modernize website terms of use, data privacy policies, and vendor agreements
Organizations should consider whether to modify their website terms of use and data privacy policies to describe the organization’s use of adtech in additional detail. Doing so could deter or help defend a future adtech class action lawsuit similar to the many that are being filed today, alleging omission of such additional details, raising claims brought under various states’ consumer fraud acts, and seeking multimillion-dollar statutory damages.
Organizations should consider adding to contracts with website vendors and marketing vendors clauses that prohibit the vendor from incorporating any unwanted adtech into the organization’s public-facing websites. That could help disprove the element of intent at issue in many claims brought under the recent explosion of adtech lawsuits.
Implications For Corporations: Implementation of these best practices is critical to mitigating risk and saving litigation dollars. Click to learn more about the services Duane Morris provides in the practice areas of Class Action Litigation; Arbitration, Mediation, and Alternative Dispute Resolution; Cybersecurity; Privacy and Data Protection; Healthcare Information Technology; and Privacy and Security for Healthcare Providers.
[1] In 2015, for example, a large study found that of 33 banks that had engaged in practices relating to debit card overdrafts, 18 endured class actions and ended up paying out $1 billion to 29 million customers, whereas 15 had arbitration clauses and did not endure any class actions. See Consumer Protection Financial Bureau (CPFB), Arbitration Study: Report to Congress, Pursuant to Dodd-Frank Wall Street Reform and Consumer Protection Act § 1028(a) at Section 8, available at https://files.consumerfinance.gov/f/201503_cfpb_arbitration-study-report-to-congress-2015.pdf. These 15 with arbitration clauses paid almost nothing—less than 30 debit card customers per year in the entire nation filed any sort of arbitration dispute regarding their cards during the relevant timeframe. See id. at Section 5, Table 1. Another study of AT&T from 2003-2014 found similarly, concluding, “Although hundreds of millions of consumers and employees are obliged to use arbitration as their remedy, almost none do.” Judith Resnik, Diffusing Disputes: The Public in the Private of Arbitration, the Private in Courts, and the Erasure of Rights, 124 Yale L.J. 2804 (2015).
[2] AAA, Consumer Mass Arbitration and Mediation Fee Schedule (amended and effective Jan. 15, 2024), available at https://www.adr.org/sites/default/files/Consumer_Mass_Arbitration_and_Mediation_Fee_Schedule.pdf; JAMS, Arbitration Schedule of Fees and Costs, available at https://www.jamsadr.com/arbitration-fees.
[3] J. Maria Glover, Mass Arbitration, 74 Stan. L. Rev. 1283, 1387 & Table 2 (2022).
[4] See, e.g., BuzzFeed Media Enters., Inc. v. Anderson, 2024 WL 2187054, at *1 (Del. Ch. May 15, 2024) (dismissing action to enjoin mass arbitration of claims brought by employees); Hoeg v. Samsung Elecs. Am., Inc., No. 23-CV-1951 (N.D. Ill. Feb. 2024) (ordering defendant of BIPA claims brought by consumers to pay over $300,000 in AAA filing fees); Wallrich v. Samsung Elecs. Am., Inc., 2023 WL 5935024 (N.D. Ill. Sept. 12, 2023) (ordering defendant of BIPA claims brought by consumers to pay over $4 million in AAA fees); Uber Tech., Inc. v. AAA, 204 A.D.3d 506, 510 (N.Y. App. Div. 2022) (ordering defendant of reverse discrimination claims brought by customers to pay over $10 million in AAA case management fees).
[5] See, e.g., Customer Data Platform Institute, “Trackers and pixels feeding data broker stores,” reporting “47% of websites using Meta Pixel, including 55% of S&P 500, 58% of retail, 42% of financial, and 33% of healthcare” (available at https://www.cdpinstitute.org/news/trackers-and-pixels-feeding-data-broker-data-stores/); builtwith, “Facebook Pixel Usage Statistics,” offering access to data on over 14 million websites using the Meta Pixel, stating, “We know of 5,861,028 live websites using Facebook Pixel and an additional 8,181,093 sites that used Facebook Pixel historically and 2,543,263 websites in the United States” (available at https://trends.builtwith.com/analytics/Facebook-Pixel).