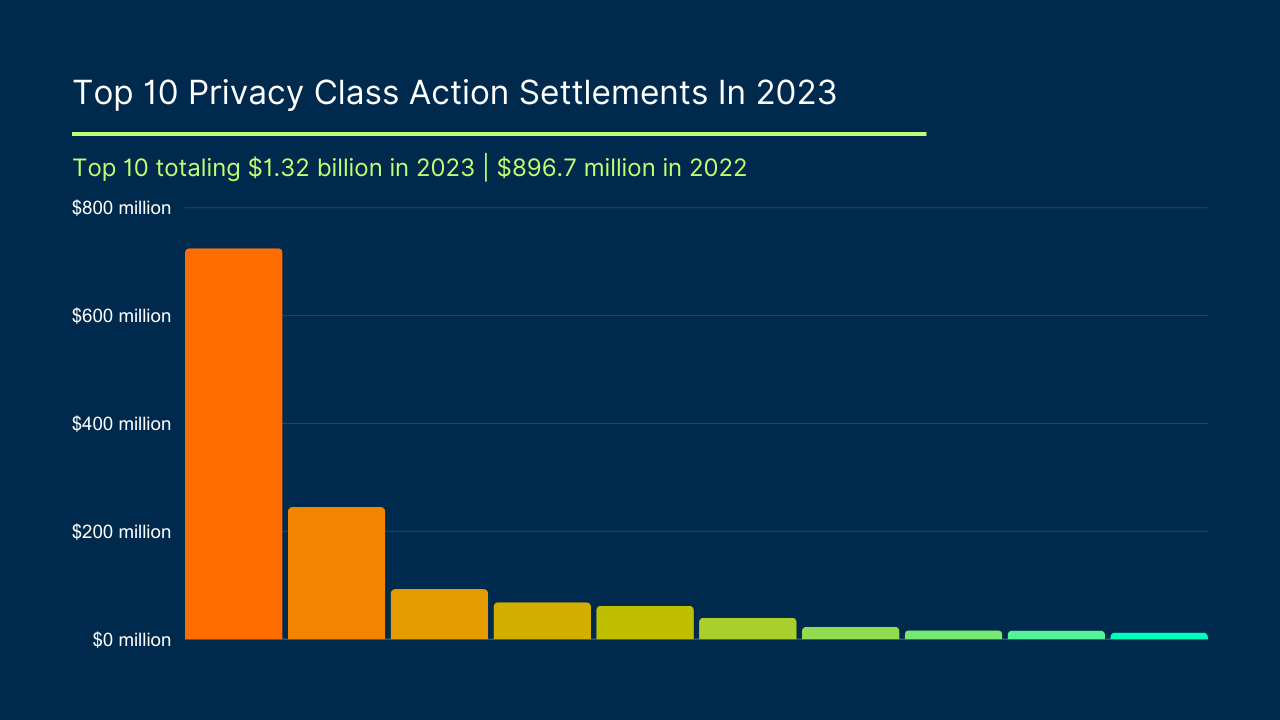
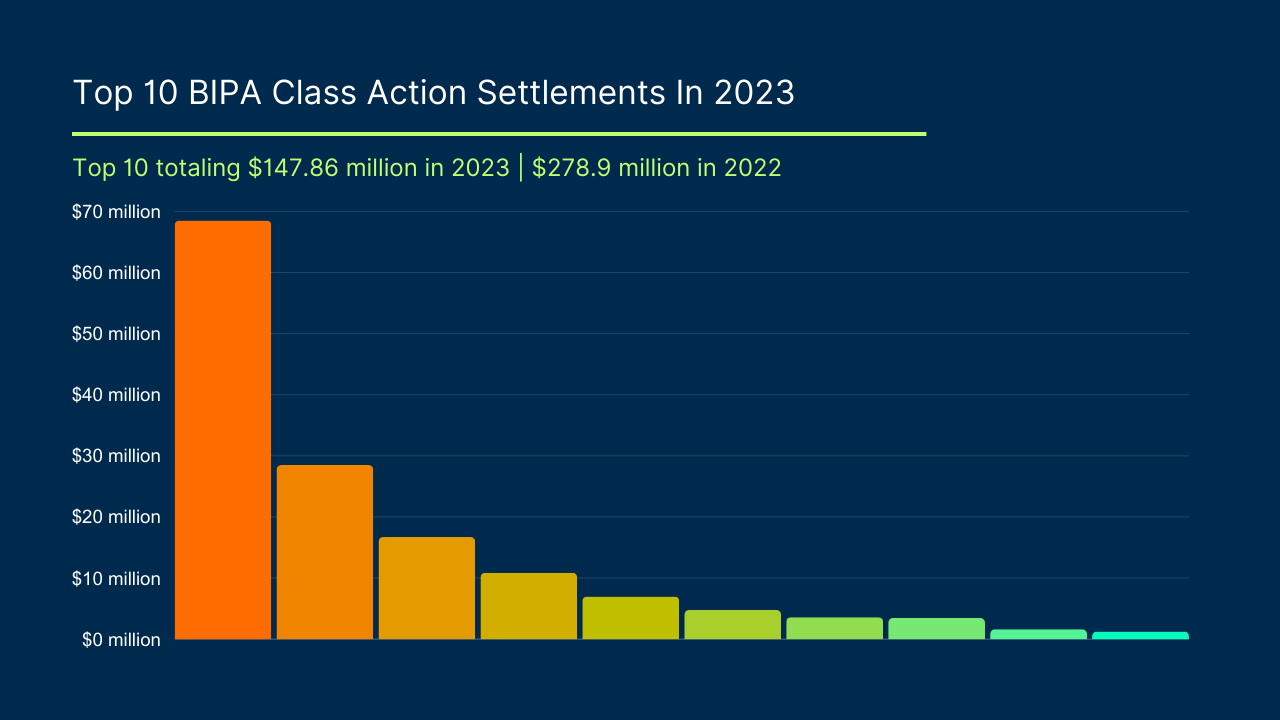
By Gerald L. Maatman, Jr., Justin R. Donoho, and Nathan Norimoto
 Duane Morris Takeaways: On July 5, 2024, in Jones, et al. v. Peloton Interactive, Inc., No. 23-CV-1082, 2024 WL 3315989 (S.D. Cal. July 5, 2024), Judge M. James Lorenz of the U.S. District Court for the Southern District of California denied a motion to dismiss a class action complaint alleging that a company’s use of a third party AI-powered chat feature embedded in the company’s website aided and abetted an interception in violation of the California Invasion of Privacy Act (CIPA). Judge Lorenz was unpersuaded by the company’s arguments that the third-party functioned as an extension of the company rather than as a third-party eavesdropper. Instead, the Court found that the complaint had sufficient facts to plausibly allege that the third party used the chats to improve its own AI algorithm and thus was more akin to a third-party eavesdropper for which the company could be held liable for aiding and abetting wiretapping under the CIPA.
Duane Morris Takeaways: On July 5, 2024, in Jones, et al. v. Peloton Interactive, Inc., No. 23-CV-1082, 2024 WL 3315989 (S.D. Cal. July 5, 2024), Judge M. James Lorenz of the U.S. District Court for the Southern District of California denied a motion to dismiss a class action complaint alleging that a company’s use of a third party AI-powered chat feature embedded in the company’s website aided and abetted an interception in violation of the California Invasion of Privacy Act (CIPA). Judge Lorenz was unpersuaded by the company’s arguments that the third-party functioned as an extension of the company rather than as a third-party eavesdropper. Instead, the Court found that the complaint had sufficient facts to plausibly allege that the third party used the chats to improve its own AI algorithm and thus was more akin to a third-party eavesdropper for which the company could be held liable for aiding and abetting wiretapping under the CIPA.
Background
This case is one of the hundreds of class actions that plaintiffs have filed nationwide alleging that third-party AI-powered software embedded in defendants’ websites or other processes and technologies captured plaintiffs’ information and sent it to the third party. A common claim raised in these cases is a claim under federal or state wiretap acts and seeking hundreds of millions or billions of dollars in statutory damages. No wiretap claim can succeed, however, where the plaintiff has consented to the embedded technology’s receipt of their communications. See, e.g., Smith v. Facebook, Inc., 262 F. Supp. 3d 943, 955 (N.D. Cal. 2017) (dismissing CIPA claim involving embedded Meta Pixel technology because plaintiffs consented to alleged interceptions by Meta via their Facebook user agreements).
In Jones, Plaintiffs brought suit against an exercise equipment and media company. According to Plaintiffs, the defendant company used third-party software embedded in its website’s chat feature. Id. at *1. Plaintiffs further alleged that the software routed the communications directly to the third party without Plaintiffs’ consent, thereby allowing the third party to use the content of the communications to “to improve the technological function and capabilities of its proprietary, patented artificial intelligence software.” Id. at **1, 4.
Based on these allegations, Plaintiffs alleged a claim for aiding and abetting an unlawful interception and use of the intercepted information under California’s wiretapping statute, CIPA § 631. Id. at *2. Although Plaintiffs did not allege any actual damages, see ECF No. 1, the statutory damages they sought totaled at least $1 billion. See id. ¶ 33 (alleging hundreds of thousands of class members); Cal. Penal Code. § 637.2 (setting forth statutory damages of $5,000 per violation). The company moved to dismiss under Rule 12(b)(6), arguing that the “party exception” to CIPA applied because the third-party software “functions as an extension of [the company] rather than as a third-party eavesdropper.” 2024 WL 3315989, at *2.
The Court’s Opinion
The Court denied the company’s motion and allowed Plaintiffs’ CIPA claim to proceed to discovery.
The CIPA is a one-party consent statute, meaning that there is no liability under the statute for any party to the communication. Id. at *2. To answer the question for purposes of CIPA’s party exception of whether the embedded chat software provider was more akin to a party or a third-party eavesdropper, the Court found that courts look to the “technical context of the case.” Id. at *3. As the Court explained, a software provider can be held liable as a third party under CIPA if that entity listens in on a consensual conversation where the entity “uses the collected data for its own commercial purposes.” Id. By contrast, the Court further explained, if the software provider merely collects, refines, and relays the information obtained on the company website back to the company “in aid of [defendant’s] business” then it functions as a tool and not as a third party. Id.
Guided by this framework, the Court found sufficient allegations that the software provider used the chats collected on the company’s website for its own purposes of improving its AI-driven algorithm. Id. at *4. Therefore, according to the Court, the complaint sufficiently alleged that the software provider was “more than a mere ‘extension’” of the company, such that CIPA’s party exemption did not apply and Plaintiffs sufficiently stated a claim for the company’s aiding and abetting of the software provider’s wiretap violation. Id.
Implications For Companies
The Court’s opinion serves as a cautionary tale for companies using third-party AI-powered processes and technologies that collect customer communications and information. As the ruling shows, litigation risk associated with companies’ use of third-party AI-powered algorithms is not limited to complaints alleging damaging outcomes such as discriminatory impacts, such as plaintiffs alleged in Louis v. Saferent Sols., LLC, 685 F. Supp. 3d 19, 41 (D. Mass. 2023) (denying motion to dismiss claim under Fair Housing Act against landlord in conjunction with landlord’s use of algorithm used to calculate risk of leasing a property to a particular tenant). In addition, companies face the risk of high-stakes claims for statutory damages under wiretap statutes associated with companies’ use of third-party AI-powered algorithms embedded in their websites, even if the third party’s only use of the algorithm is to improve the algorithm and even if no actual damages are alleged.
As AI-related technologies continue their growth spurt, and litigation in this area spurts accordingly, organizations should consider in light of Jones whether to modify their website terms of use, data privacy policies, and all other notices to the organizations’ website visitors and customers to describe the organization’s use of AI in additional detail. Doing so could deter or help defend a future AI class action lawsuit similar to the many that are being filed today, alleging omission of such additional details, raising claims brought under various states’ wiretap acts and consumer fraud acts, and seeking multimillion-dollar and billion-dollar statutory damages.